Ultra-Long Fiber Lasers for Secure Key Distribution
Introduction
The distribution of a secret key is most probably the main Achilles heel of any secure communication system. To establish completely secure information transfer it is necessary for the two users to share a secret key, known only to them, before the communication can take place. In many practical scenarios, especially when the two users are separated by a large distance, this requirement is difficult to realize because secure transmission of the key requires a previously shared (additional) key. This loophole was one of the main incentives behind the attempts to develop physically (as opposed to algorithmically) secure key distribution schemes based on the fundamental properties of quantum mechanics. Although ideally such communication protocols are perfectly secure6, their practical implementation is not simple. Noise and attenuation in the quantum channel reduce significantly their efficiency, especially from the range and data rate aspects. Theoretical and experimental studies show that channel attenuation, noise and detectors dark-counts limit the key-establishing rates and the operational ranges of QKD systems.
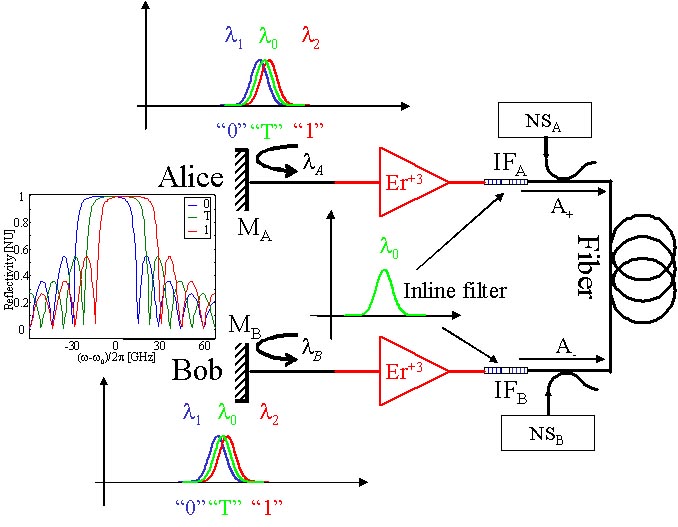
The idea is to develop a new concept for key distribution, based on establishing a laser oscillation between sender and receiver. The suggested architecture offers potential key-establishing rates which are larger by several orders of magnitude than those of the currently demonstrated QKD systems, especially at long communication ranges. The schematic of the system is presented below:

The system consists of a long erbium-doped fiber laser with Alice at one end and Bob on the other. In the example depicted in figure, Bob and Alice can, each, choose independently a mirror from a set of three mirrors (one set at each end), labeled T, 1 and 0 (see the inset of the Fig), and use it as the laser reflector at their end. Each of the three mirrors in a set has its peak at a different frequency. The T mirror is centered on w0, mirror 1 it is centered on w0+dw and mirror 0 is centered on w0-dw. The erbium-doped amplifiers (EDFA) provide the optical gain for the laser and the inline filters IFA and IFB are narrow-band filters centered at w0. Each communication cycle (i.e., the generation of a bit for the key) starts with Alice and Bob placing their mirror at w0 (T). This phase resets the symmetry of the system and establishes synchronization. Next, they, each, randomly select a bit (i.e., 0 or 1) and switch-on the appropriate mirror. The laser gain is maintained at a level such that if they pick different bits, there is sufficient gain for the laser to lase at w0 but at a lower amplitude compared to the T state. If they, both, choose 1 the lasing wavelength shifts to w0-dw and if they choose 0 the lasing wavelength shifts to w0+dw.
An eavesdropper who is not allowed to see the
mirrors but measures the power in the laser might be able to determine that one
person chose mirror 0 and the other chose mirror 1, but she could not tell which
person chose which mirror. As a result, she would not have enough information to
determine what numbers Alice and Bob are exchanging.
A sensitive enough measurement of the light in the fiber could theoretically
reveal the information that Alice and Bob are transmitting, but by including
filters in the system and injecting random noise into the fiber it is possible
to arbitrarily increase the technical challenges a would-be snooper faces in
trying to eavesdrop. Unlike quantum communication, which is potentially
absolutely secure, the fiber laser system could be designed to be just secure
enough to ensure that communications are secret while keeping material costs
down and long distance transmission speeds up, thus making it intriguing and
possibly alternative technology to QKD.